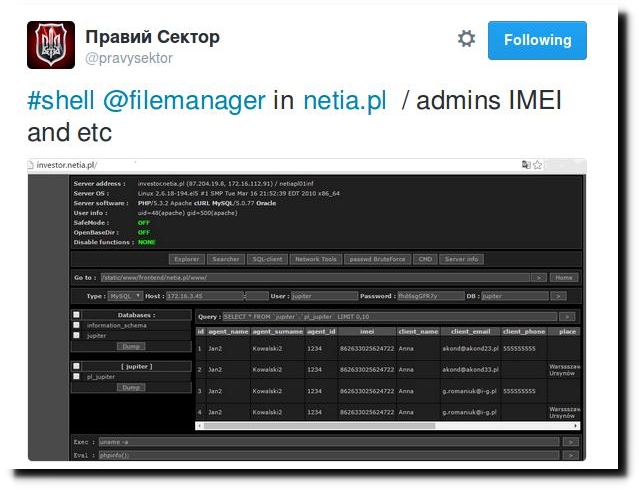
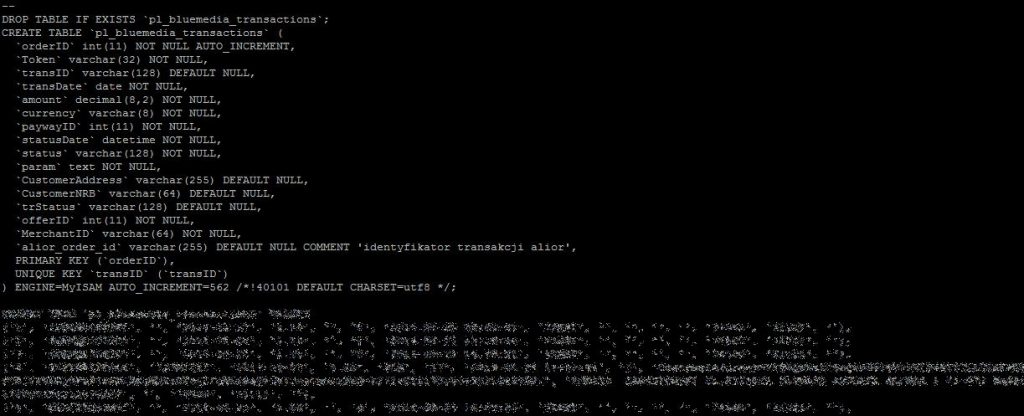
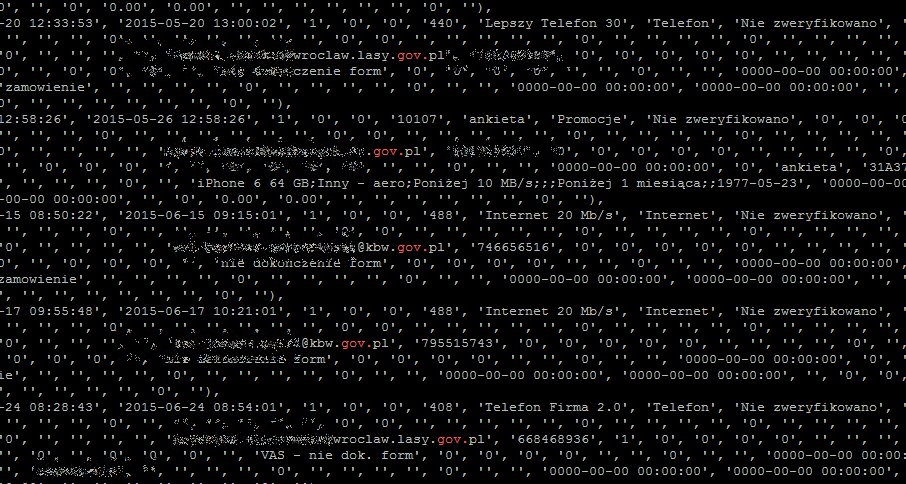
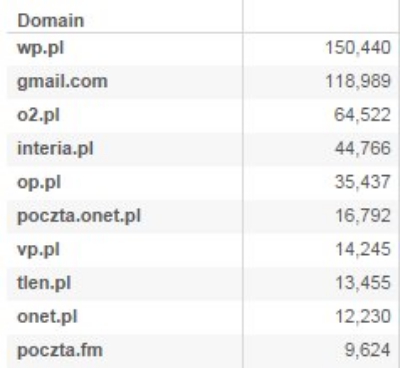
Sitting in a brightly lit apartment in Brooklyn, an American hacker who asked Al-Monitor to call him Alex scribbled down a
dizzying array of cyberstrikes
between the United States/Israel and Iran since 2010. The page was fast
being covered in Alex’s rushed handwriting, and his eyes glimmered with
excitement.
“They’ve gotten incredibly sophisticated,” he said as he marveled at the speed at which Iranian hackers have been able to create a defensive and offensive arm against Western cyberattacks. Yet, as he neared 2015
on his ad hoc timeline, his pen began to slow.
“With the Iran [nuclear] deal, we saw a parallel cooling down of
attacks in the cyberworld.
The nuclear deal has not only opened discussion with the Iranians on
nuclear issues, but it has created a mutual detente in the cyberworld,
and that’s huge, because cyberwarfare between Iran and the West was
getting to
really bad levels.”
David, an Iranian-American internet
security specialist who spoke to Al-Monitor on condition of anonymity,
agreed. He said, “Before the Iran deal, we were witnessing a heightened
level of cyberwarfare between Iran and the US/Israel. It was getting to a
very [worrisome] level, as Iran’s capabilities had increased
exponentially in a very short period of time. But the Iran deal has put a
halt to all of this.” David's employer is one of the leading US
firms that monitor Iranian cyberactivity.
Until the 2011
emergence of Stuxnet,
a malicious computer worm reportedly built by the United States and
Israel to sabotage Iran’s nuclear program, Iranian cyberstrike
capabilities were virtually nonexistent. Until then, the Islamic
Republic was focusing on its own citizens. Local hackers contracted by
the authorities spent time
monitoring domestic netizens. With the advent of the 2009
Green Movement, Iran officially created the “Iranian Cyber Army,” further tapping into the extensive surveillance network that
German firm Siemens had installed in the country. The key stakeholders in the Cyber Army include the Islamic Revolutionary Guard Corps and the
Basij paramilitary militia.
To counter Stuxnet, Iran began pouring cash into both defensive and
offensive cybercapabilities. David, the internet security specialist,
said in this regard, “It wasn’t until Stuxnet that Iran realized it
could use cybercapabilities as a weapon on such a large scale.”
“Iran went from being a nuisance in the cyberworld to starting big
cyberattacks around the world,” Alex, the hacker, said. “They began
stealing encryption keys and attacking US banks. But the biggest was
Operation Shamoon [2012]
in which Iranian hackers were able to completely
bring down Saudi Aramco, targeting 30,000 Saudi Aramco workstations.
The rate at which they were able to expand caused paranoia in
cybersecurity circles across the world, but especially in the Gulf
countries.”
He added, “Iran’s attack against Aramco was no joke — it brought down the entire system. That’s huge.”
The West and Israel reportedly targeted Iran with four pieces of cyberweaponry between 2010 and 2012: Stuxnet,
Duqu,
Flame and
Gauss. Each time, the Islamic Republic retaliated almost tit for tat, stealing encryption keys and certificates. In 2013,
Israel said Iran was constantly attacking its power grid and water systems.
David said, “It was with
Operation Cleaver
[2014] that targeted US defense contractors, energy firms and
educational institutions, that the United States began to really look at
and study Iran’s cyberactivities. We concluded that Iran’s
cyberactivities are now on par with China.” The FBI
issued warnings about Operation Cleaver, which was known to have hit US Navy servers and caused breaches in other major targets.
“Unlike the Chinese or Russian cyberarmies — which stage massive
attacks like a conventional army would in the real world — the Iranian
Cyber Army works in a much more guerrilla fashion. They work patiently
and slowly, and that’s why it is much harder to detect their activity
until they have completely hacked a system,” David said. “The Iranian
hackers are experts at 'personifying' by creating fake profiles on
social media sites and slowly connecting to people. They establish
relationships with users on other ends, and after a long period of time
they will hack the system. It’s ingenious, because there is no way to
detect this. They did a hack on Gmail and were able to get a lot of
personal information in the same way.”
Unlike China and Syria, for instance, where cyberwarriors are
official members
of their country’s military and intelligence units and report to work
every day, Iran keeps a bit of a distance from its hackers. In this
vein, the
Islamic Republic
rather operates along the lines of the US model, in which private
companies and hackers are mostly contracted to do the work, according to
a
2013 report
by California-based cybersecurity firm FireEye Inc. Like the United
States and its National Security Agency (NSA), Iran also has
cybercapabilities in certain intelligence bodies, but for the most part it relies on outside contractors.
One of those firms is Ajax Security, a private security company in
Iran monitored by FireEye. It is thought to be one of the leading
enablers of the Islamic Republic’s quest to enhance Iranian
cybercapabilities. Ajax Security is thought to be behind “
Operation Saffron Rose,” a series of attacks that features
spear-phishing
emails as well as spoofed Microsoft Outlook Web Access and virtual
private network pages. The operation also includes trolling for user
credentials from defense contractors and other members of the defense
industry. Ajax Security is additionally active in helping the Iranian
authorities monitor activists by luring them with legitimate
anti-censorship tools rigged with malware. According to the FireEye
report, Ajax Security has become the first Iranian hacking group known
to use custom-built malicious software to launch espionage campaigns.
In a 2014
interview with Reuters,
former CIA and NSA director Michael Hayden said, “I've grown to fear a
nation-state that would never go toe to toe with us in conventional
combat and that now suddenly finds they can arrest our attention with
cyberattacks.”
Alex said he agrees with Hayden’s assessment. “That’s why the Iran
deal has been so significant. These cyberattacks were happening because
the United States and Iran distrusted each other and we were after their
nuclear program, so they were retaliating in kind. The Iran deal has
slowed all of this down and hopefully will ensure that we don’t have to
be attacking each other in this fashion,” he said.